Maritime Cybersecurity Threat Contextualization – Preparing for Autonomous Ships
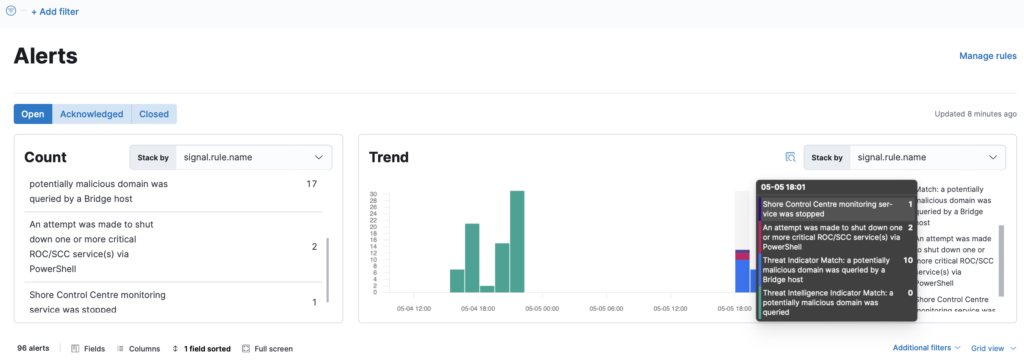
Figure 1. Sequential risk element alerts in a multi-stage attack in ARPA-project’s taxonomy use case.
Background
The maritime sector has always been a critical component of the global economy, facilitating the transportation of goods (over 90% of global trade) and people across the world. Today the maritime industry is slowly moving towards autonomous ships equipped with modern systems that allow them to operate without human intervention. A subproduct of this deveopment – autonomous transportation of goods – is expected to fundamentally change maritime traffic as autonomous ships start to navigate the same seas with the conventional ships [1]. While this is a significant step forward, it also brings various cybersecurity threats that need to be addressed. In this blog post, we will discuss how cybersecurity situational awareness and cyber threat intelligence can help prepare for these threats and what steps were taken in the ARPA project.
Cybersecurity Situational Awareness and Cyber Threat Intelligence
The maritime sector has unique characteristics that make it an attractive target for cybercriminals. Ships and vessels are often at sea for extended periods, making them difficult to monitor and protect. Additionally, they rely on a complex network of operational technology (OT) systems, including navigation, propulsion, and communication systems, which are connected to the internet and vulnerable to cyber attacks.
For the decision makers and stakeholders in the maritime industry, it is essential to understand the concepts cybersecurity situational awareness and cyber threat intelligence. Cybersecurity situational awareness involves the monitoring and analysis of activities in the cyber environment to identify, understand, and respond to cybersecurity incidents. Cyber threat intelligence (CTI), on the other hand, refers to the knowledge and insights gained from the analysis of cyber threats, previous cyber attacks and threat actors, which can be used to inform decision-making and enhance security and preparedness.
For the maritime industry cybersecurity situational awareness and cyber threat intelligence are vital to protect its assets, reputation, and stakeholders. By utilising these two concepts, the maritime industry can better prepare and protect itself from cybersecurity threats. In this project, TUAS MISP was used as the sharing platform for cyber threat intelligence information retrieved from open sources.
Taxonomies for Operational Technology (OT) and Maritime systems
To better understand and describe the threats facing the maritime sector, it is essential to identify and classify the OT systems present in ships and vessels. Taxonomies are useful tools for organising and categorising these systems, but only a handful of those have been developed specifically for the maritime industry.
One taxonomy commonly used in the maritime and offshore industry is the SFI coding and classification system international standard [2]. The SFI group system consists of eight groups each divided into ten subgroup, covering the ships’ various components, e.g. thrusters, ballast pumps, dynamic positioning systems, navigation and communication systems, etc.
Another taxonomy is the DNV rules for ships, part 6 chapter 5, including additional class notations for ship functions critical to cyber security [3]. Also the ISO/IEC 62443 series of standards provide taxonomy in form of terminology, concepts and models, which are focused on the cybersecurity of industrial automation and control systems [4, 5].
However, each of these taxonomies have limitations when it comes to capturing the full range of OT systems present especially on modern ships and vessels. Therefore, a new, more comprehensive taxonomy was needed to more efficiently contextualise the threats targeting the maritime sector.
To address this need, a new, maritime systems taxonomy was created in the ARPA project that followed the MISP standard [6]. Following MISP standard not only allowed for the immediate utilisation of the taxonomy within MISP, but also guaranteed compatibility with all other MISP instances, which made it possible to share and distribute the taxonomy with partners and information sharing communities. The new taxonomy included several categories of systems, including propulsion, steering, ship’s environmental control systems, as well as communication and security systems. The new taxonomy provided a more detailed and compehensive view of the OT systems but also recreational consumer systems present on moderns ships and vessels. By categorising these systems, we were able to better understand the cybersecurity threats that may target them, as well as produce CTI early warning data for the maritime industry and supply chain. Figure 2. depicts the concept for utilising TUAS MISP and the Maritime OT taxonomy in MASS (Maritime Autonomous Surface Ship) threat hunting scenario.
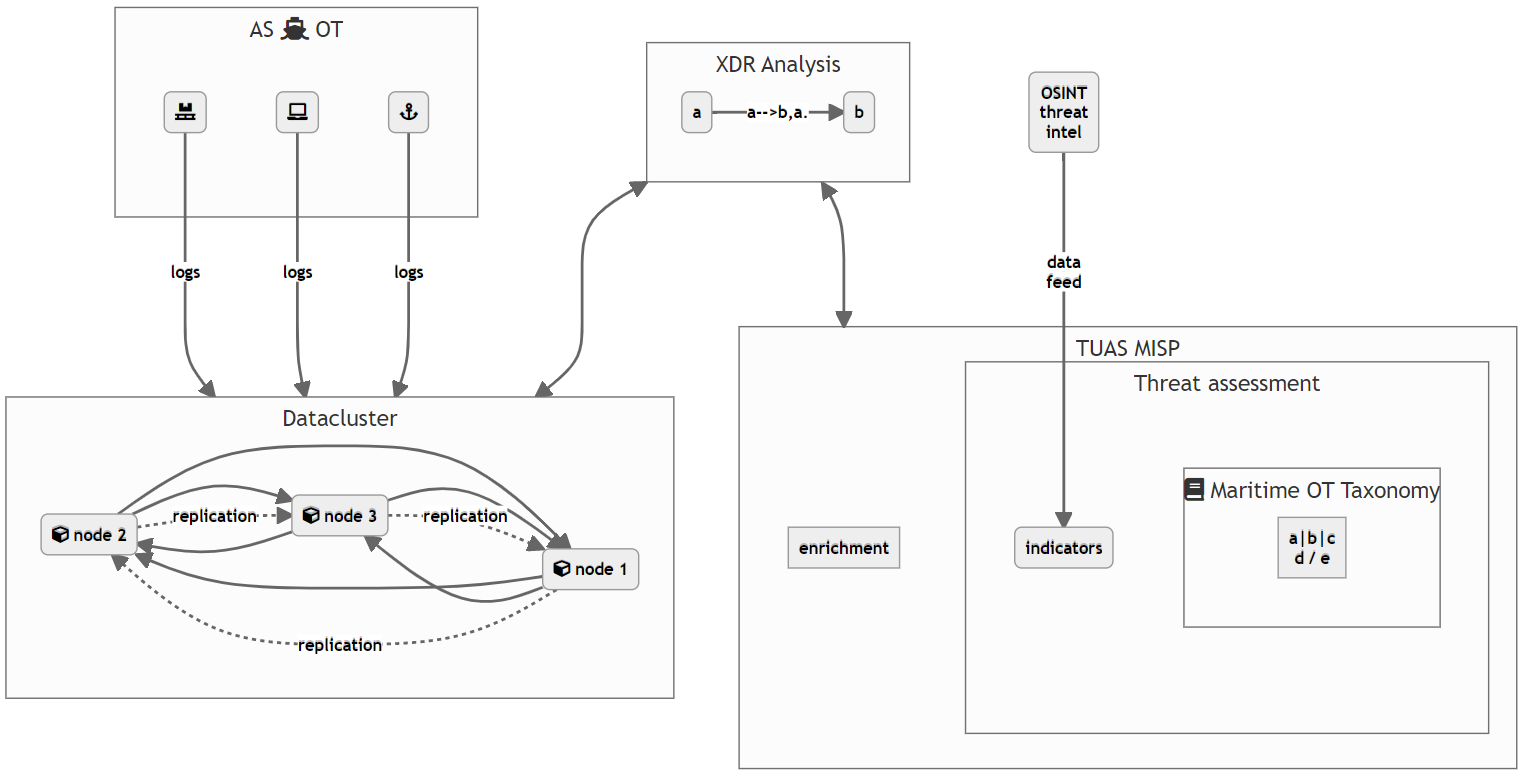
Figure 2. Maritime OT taxonomy and TUAS MISP component in threat hunting toolset – conceptual drawing
Use cases
We set out to describe a handful of use cases with which to test the new taxonomy. More specifically, the goal was set to assess the taxonomy’s usability and effectiveness in identifying and categorising the various systems targeted in maritime-OT-specific cyber attacks.
According to a recently published threat analysis report from the European Union Agency for Cybersecurity, ENISA, the threat actor group delivering the most attacks (54%) against the transport sector is cybercriminals. This was observed in their 20-month-long threat analysis of the transport sector’s four subsectors aviation, maritime, railway and road. The report concluded that the attacks in the maritime domain was often politically motivated, targeting port authorities, port operators and manufacturers, and perpetrated by nation state or state sponsored attackers, indicative of the interest of nation state actors for causing operational disruption. [7]
Following the maritime trend from [7], the threats and scenarios related to maritime and smart shipping from [7, 8] and impact potential from [9, 10], we narrowed our scope to shallow and confined waters, for which we then created three use cases.
We used the TUAS MISP CTI platform to conduct the actual tests. The first use case was a shipping company spearphishing campaign. The second use case involved an attack against an LNG tanker’s ballasting tank stabilisation system, where the attacker’s goal was to manipulate the vessel’s stability, causing her to become unstable and potentially leading to an accident. The third use case involved an attack against a car and passenger ferry’s propulsion system, in which the attacker was able to disable the vessel’s propulsion system, leaving her stranded in the water.
Inside the MISP platform a completely new threat actor group was also described. This included describing their tactics, techniques, procedures and technical toolset all as objects following the MISP standard. This allowed for better and more realistic contextualisation of the targeted threat in each use case, as well as correlation and visualisation of the accumulated threat posed by this maritime-specific threat actor group.
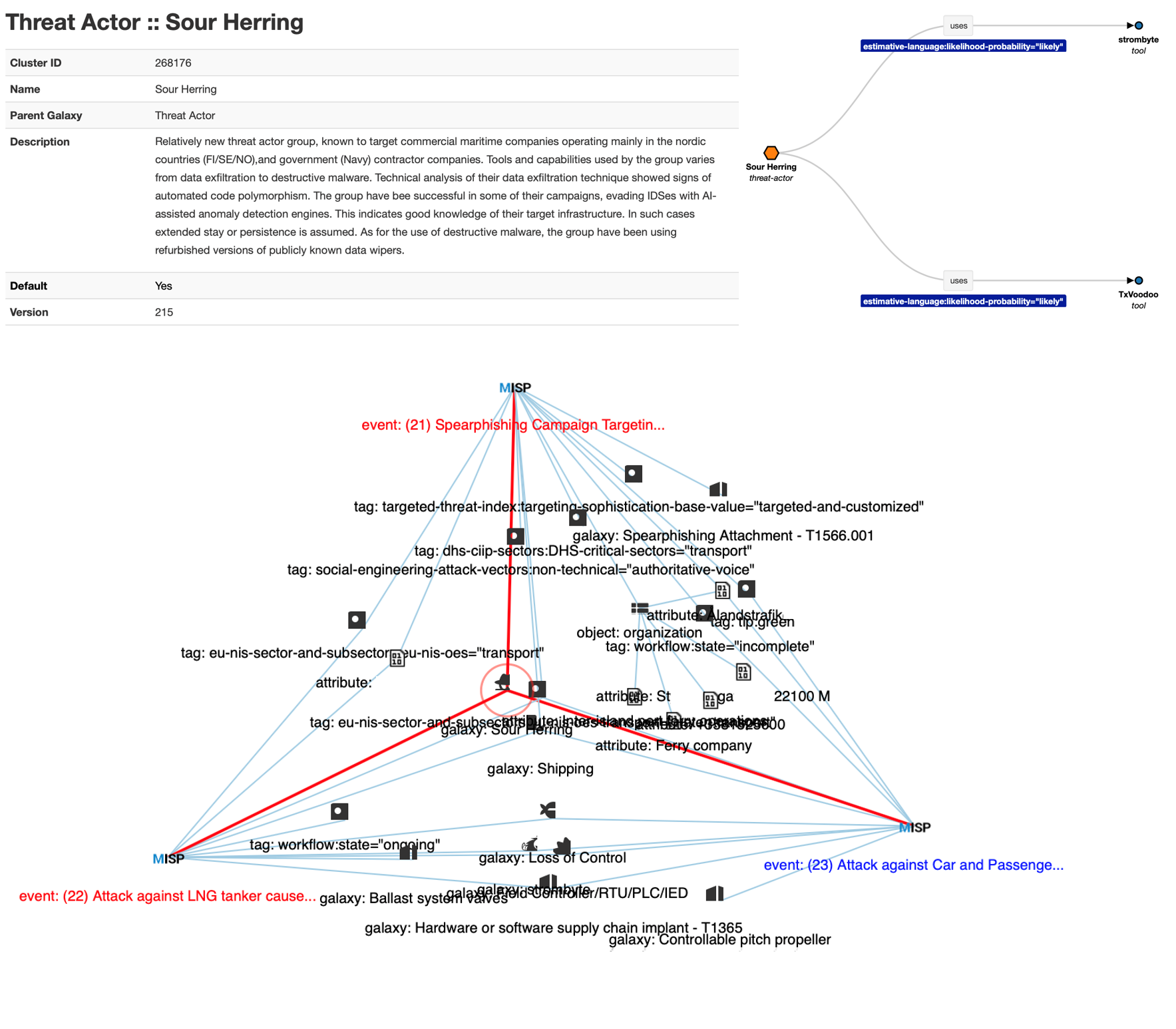
Figure 3. New threat actor and use cases event correlation shown in TUAS MISP CTI
CTI Data Integration
The maritime industry, like many other industries, has a need to ensure that their systems and operations are secure from cyber threats. Cyber Threat Intelligence (CTI) data can be a valuable resource for enhancing the security of maritime operations. By using CTI data, maritime companies can stay informed about the latest threats and vulnerabilities affecting their systems and operations. This information can be used to improve the effectiveness of security controls and defenses, as well as enhance the ability of security personnel to respond to incidents and threats.
One key way in which CTI data can be used is to integrate it into defensive systems. This involves using the CTI data to inform the configuration of security controls and defenses, such as firewalls, intrusion detection systems, and other security devices. For example, if a new threat is identified that targets a particular type of system or application, security controls can be configured to detect and block that threat. This can help to reduce the risk of successful attacks and improve the overall security posture of the organisation.
We verified the compatibility of our taxonomy by integrating the TUAS MISP platform with two external systems, both consuming the newly produced CTI, that was described with contextual information from the maritime taxonomy. The first integration was an Extended Detection and Response (XDR) platform, commonly used via SOC service providers and centres for threat hunting activities – technical analyses of sequential events related to threats that traditional signature-based tools cannot detect. The second integration was a SOC orchestration tool, which was used to conduct collaborative team activities during threat hunting, allowing several parallel event investigations.
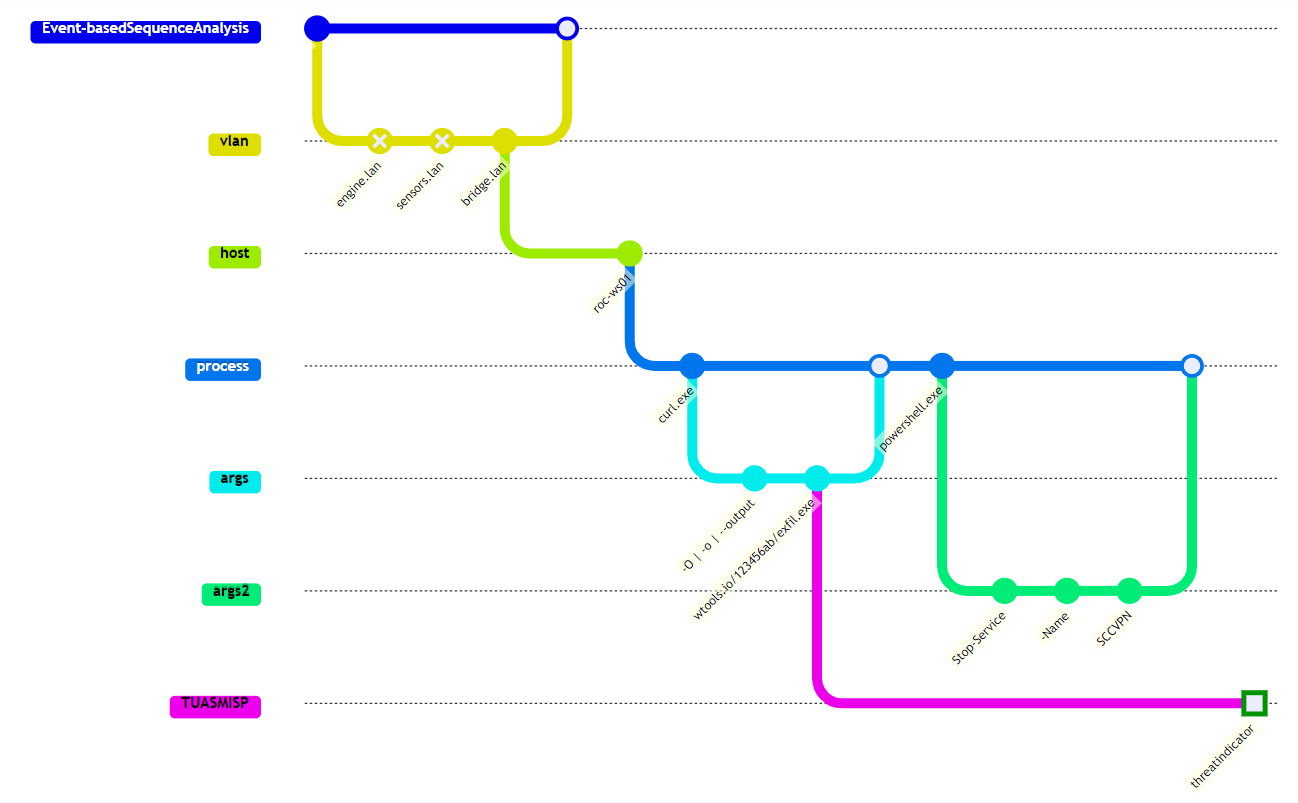
Figure 4. TUAS MISP event reporting for sequential threat hunting analysis.
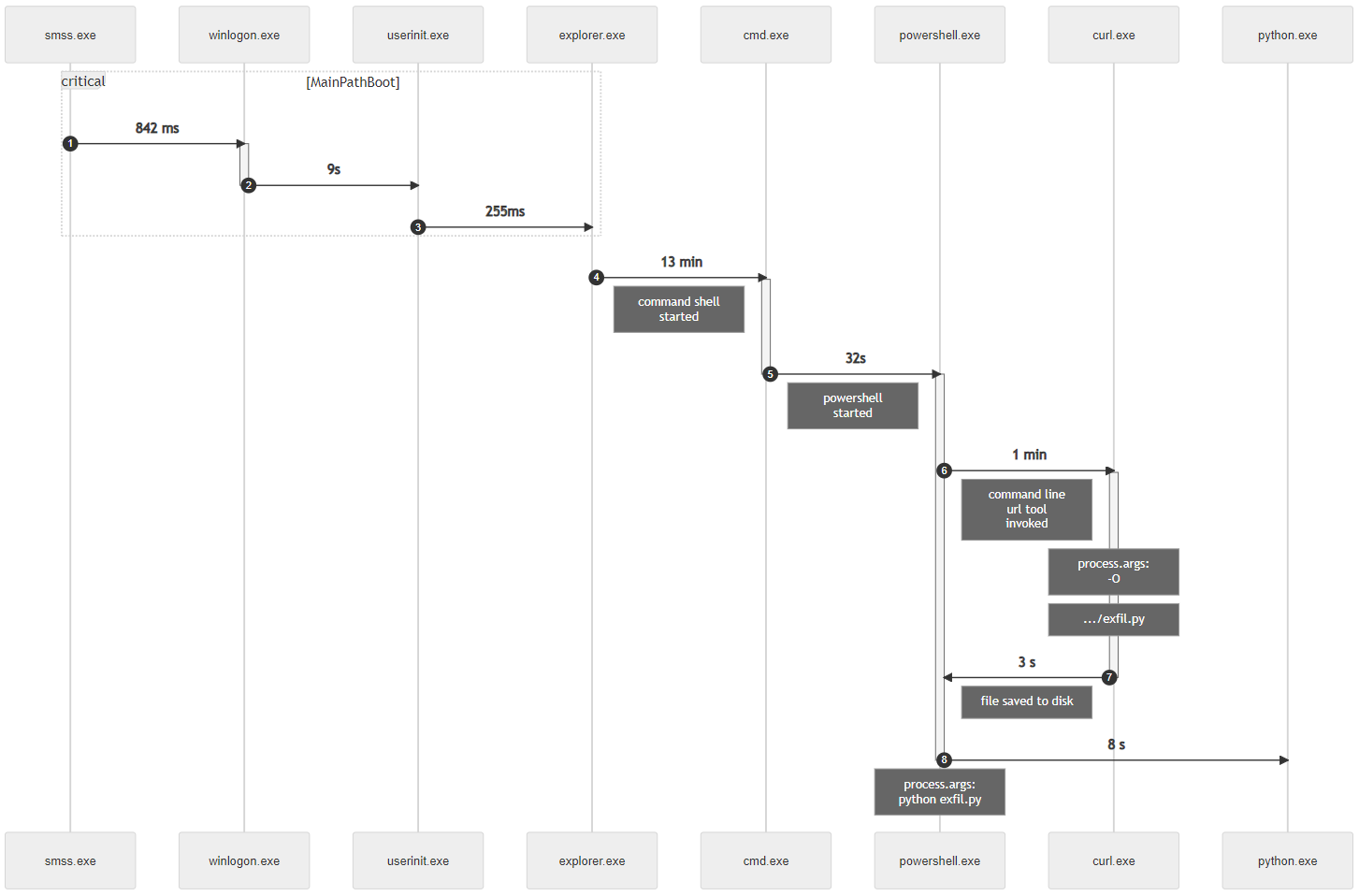
Figure 5. XDR alert transformed into TUAS MISP event analysis
Conclusion
The maritime systems taxonomy developed in this project can be a valuable tool for describing the threat landscape facing maritime industry. Updated with new and topical data from new sources, e.g. from [11], the taxonomy can be extended also to describe threats against autonomous ships. Following standardised structure in the taxonomy’s model declarations allows for the utilisation of maritime-specific CTI in external information systems. These include e.g. information sharing systems using common threat expression formats, such as STIX and TAXII, as well as various frameworks especially designed for OT or IACS threat hunting [12, 13].
Overall, the development of this taxonomy represents an important step forward in enhancing the cybersecurity posture of the maritime industry, and in preparing for the challenges of the future.
Author:
Jani Vanharanta, Senior Lecturer, Turku University of Applied Sciences
References:
[1] Cho, S., Orye, E., Visky, G., Prates, V. ”Cybersecurity Considerations in Autonomous Ships.” The NATO Cooperative Cyber Defence Centre of Excellence, CCDCOE, Tallinn, EE, 2022.
[2] SpecTec. SFI Coding and Classification System for Ship Information, SFI Group System. Retrieved 23.3.2023 from https://www.spectec.net/news/article/sfi-standard.
[3] Det Norske Veritas, DNV (2021). Rules For Classification: ships – DNV-RU-SHIP Pt.6 Ch.5. Edition 2021. Retrieved 2.6.2022 from https://rules.dnv.com/docs/pdf/DNV/RU-SHIP/2021-07/DNV-RU-SHIP-Pt6Ch5.pdf.
[4] B. C. Belev, “Purdue Model Implementation in the Shipping Control Systems,” 2022 10th International Scientific Conference on Computer Science (COMSCI), Sofia, Bulgaria, 2022, pp. 1-4, doi: 10.1109/COMSCI55378.2022.9912594.
[5] International Organisation for Standardisation. (2013). Industrial communication networks. Network and system security. Part 1-1: Terminology, concepts and models (Technical Specification ISO/IEC/TS 62443-1-1). Retrieved 23.3.2023 from https://online.sfs.fi.
[6] MISP Published Standards. MISP Standards. Retrieved 23.3.2023 from https://misp-standard.org/standards
[7] ENISA. European Union Agency for Cybersecurity. (2023). ENISA Transport Threat Landscape, March 21. 2023. Available from: https://www.enisa.europa.eu/publications/enisa-transport-threat-landscape.
[8] Furumoto, K., Kolehmainen, A., Silverajan, B., Takahashi, T., Inoue, D. and Nakao, K. Toward Automated Smart Ships: Designing Effective Cyber Risk Management. Proceedings of the 2020 International Conferences on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData) and IEEE Congress on Cybermatics (Cybermatics), Rhodes, Greece, 2020, pp. 100-105, doi: 10.1109/iThings-GreenCom-CPSCom-SmartData-Cybermatics50389.2020.00034.
[9] The Mitre corporation. Matrix | MITRE ATT&CK™ ICS Matrix. Available from: https://attack.mitre.org/matrices/ics/. Accessed 23.3.2023.
[10] Kovanen, T., Pöyhönen, J., Lehto, M. (2021). Kovanen, T., Pöyhönen, J., Lehto, M. (2021). ePilotage System of Systems Cyber Threat Impact Evaluation. Proceedings of the 16th International Conference on Cyber Warfare and Security ICCWS2021, pp. 144-153.
[11] International Organisation for Standardisation. (2022). Ships and marine technology — Vocabulary related to autonomous ship systems (Technical Specification ISO/IEC/TS 23860:2022). Retrieved 23.3.2023 from https://www.iso.org/standard/77186.html.
[12] Jadidi, Z. & Lu, Y. (2021). A Threat Hunting Framework for Industrial Control Systems, in IEEE Access, vol. 9, pp. 164118-164130, doi: 10.1109/ACCESS.2021.3133260.
[13] Arafune, M., Rajalakshmi, S., Jaldon, L., Jadidi, Z., Pal, S., Foo, E., Venkatachalam, N. (2022). Design and Development of Automated Threat Hunting in Industrial Control Systems. Proceedings of the 2022 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events (PerCom Workshops), Pisa, Italy, 2022, pp. 618-623, doi: 10.1109/PerComWorkshops53856.2022.9767375.
